New Research Shows Why Employees Click On Phishing Emails
First-ever Large Scale Self-Reported Phish Click Study highlights growing risk from AI-improved phishing
First-ever Large Scale Self-Reported Phish Click Study highlights growing risk from AI-improved phishing.
A new large-scale study from Beauceron Security gives insights into the reasons why thousands of people clicked on a phishing simulation test, and the results carry urgent lessons for organizations fighting AI-powered cybercrime.
The first-ever large-scale survey of self-reported phishing behavior analyzed responses from 6,293 employees across 257 organizations between December 2023 and August 2025. The survey was assigned after they had clicked on a simulated phishing email sent by the Beauceron Platform.
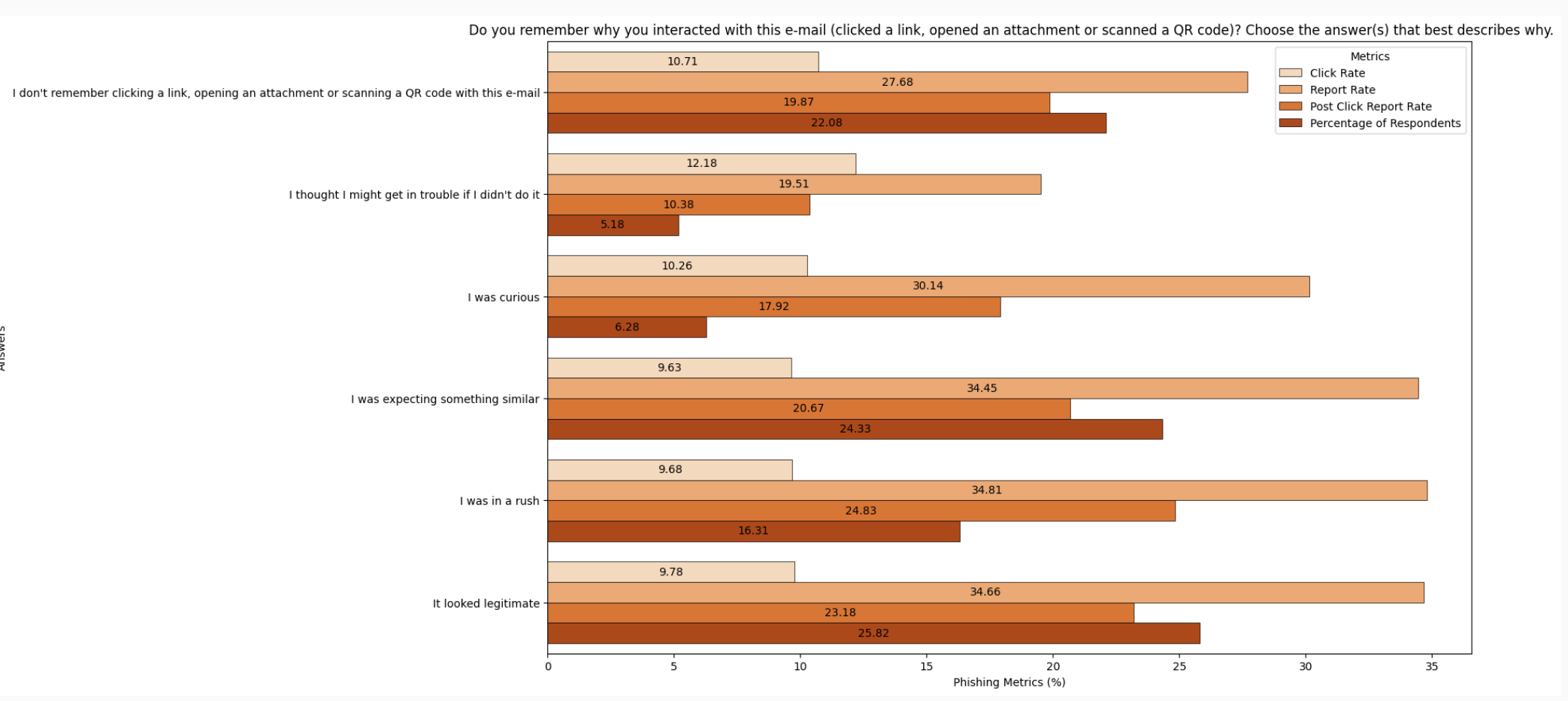
The survey found that phishes that looked legitimate or that were similar to what people were already expected to receive account for half of all clicks, while people on “email autopilot,” rushing through crowded inboxes, account for nearly 40% of all clicks.
The study also offers hope: employees who clicked on a phishing simulation and completed this survey, combined with follow-up training, reduced their subsequent click rates by as much as 62%.
Here are some of the most compelling insights from the data collected through this survey:
Half of all phishing simulation clicks by employees are caused by lures that look legitimate or were based on something the targets were expecting.
Nearly 40% of all clicks come from people operating on autopilot (22%) or who admit they were rushing. Nearly 22% of employees who interacted with a phishing link don’t remember clicking, opening an attachment, or scanning a QR code. Nearly one in five, or 16% of all clicks were due to rushing. Both response groups indicate a need for people to slow down when interacting with messages.
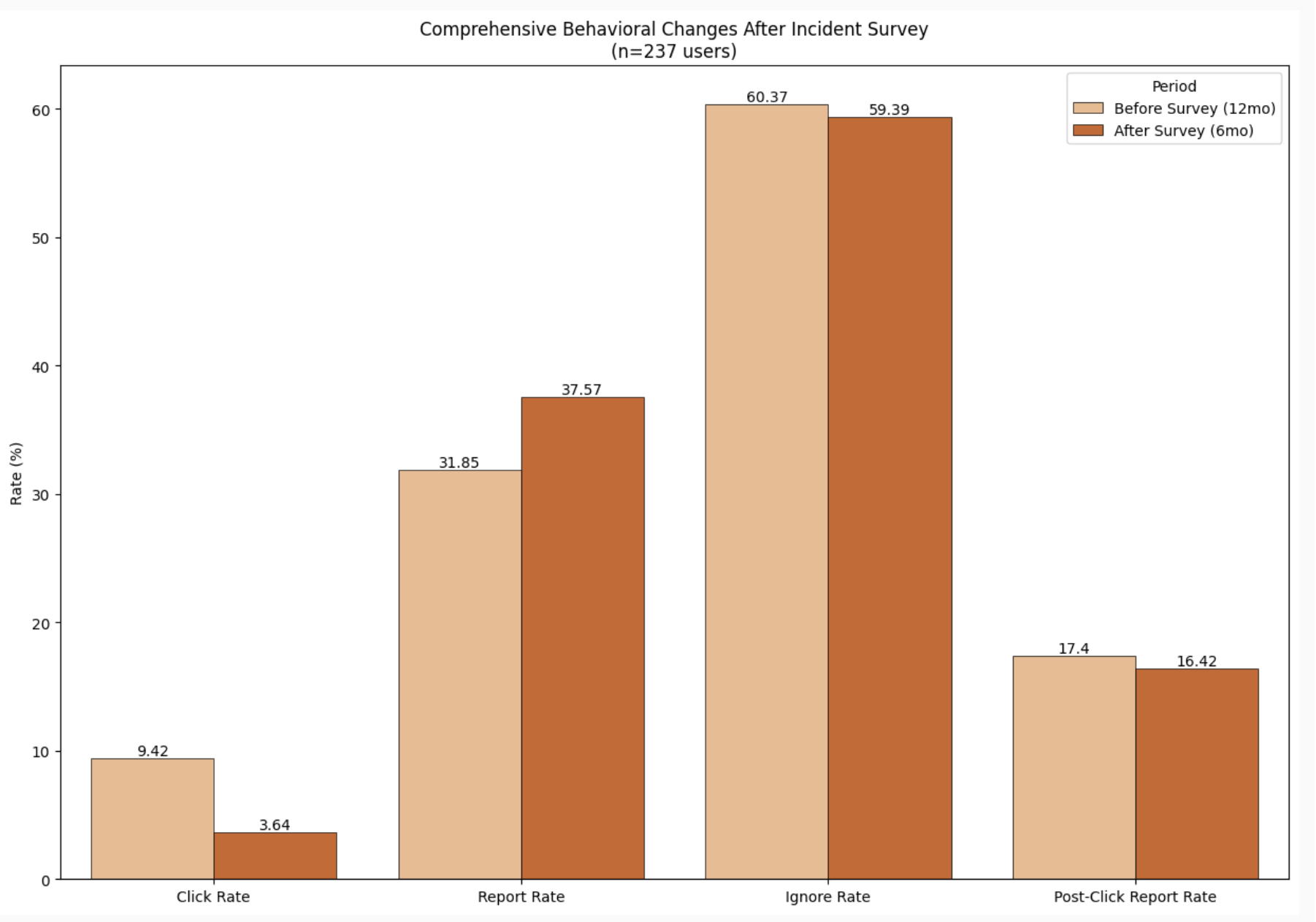
Employee Click Rate was 62% lower on average in the six months following the survey (and assigned training) compared to the 12 months before the survey. The Report Rate of employees who completed the study was 18% higher on average in the six months following the survey compared to the 12 months prior to the survey.
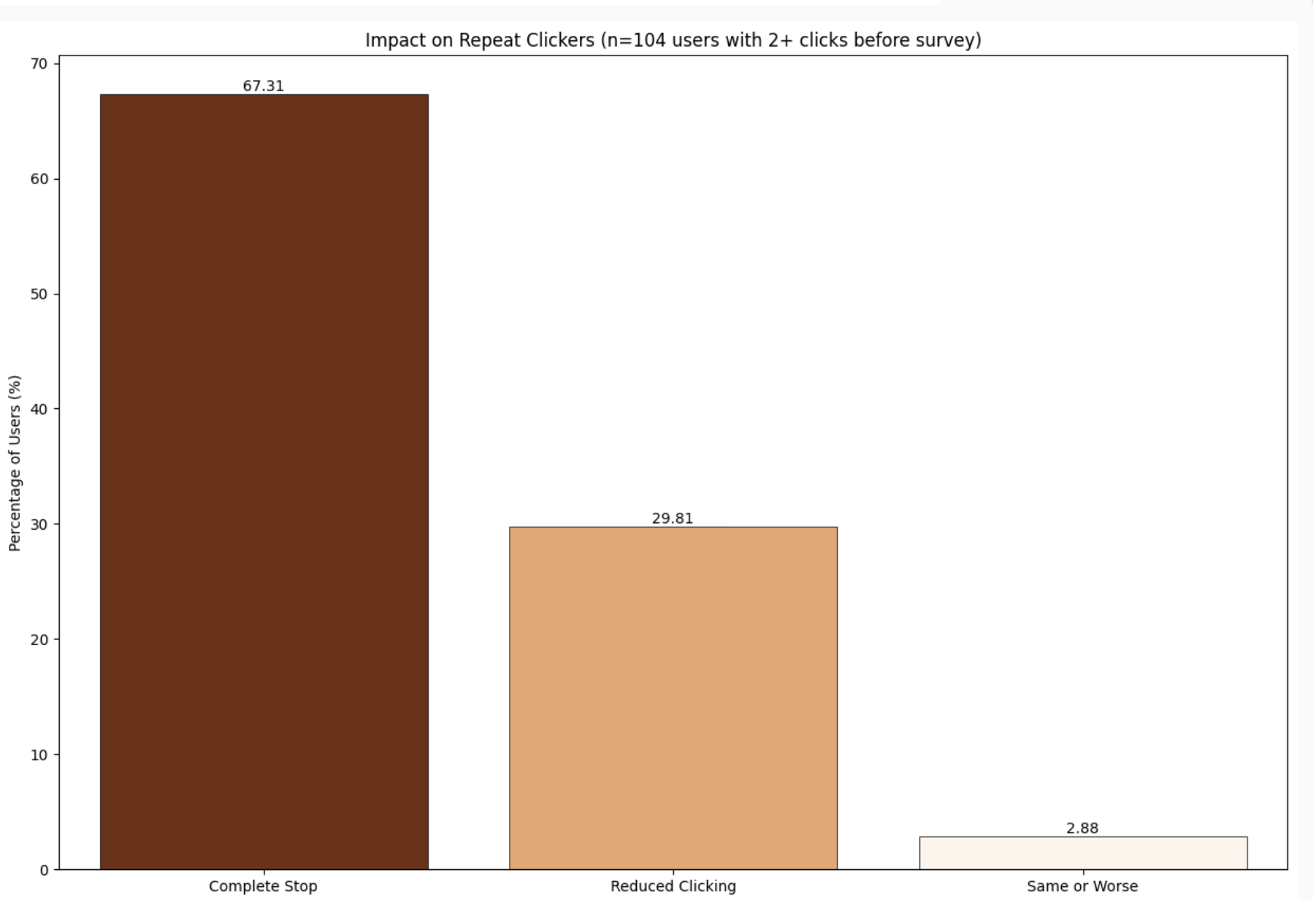
Repeat clickers benefited even more from being asked to think about the experience through the survey. Almost two-thirds of the employees who had more than one simulated phishing click incident in the preceding 12 months did not have any incidents in the six months following the survey.
Beauceron Security developed the survey with help from an independent academic researcher and client feedback.
The results come from 6,293 people at 257 organizations, primarily (but not exclusively) headquartered or based in Canada. Survey responses were collected between December 15, 2024, and August 30, 2025. Phishing simulation results from December 2023 to August 30, 2025 were also analyzed.
“The trends in this study tell us two important things. First, AI-backed phishing that improves design quality and optimizes lures for the target audience will continue to cause havoc for organizations,” says David Shipley, CEO of Beauceron Security.
“Second, effective phishing simulation training should include the opportunity for people to reflect on their experience as well as meaningful follow-up training. Phishing simulations and security awareness can make a difference, as we’ve shown, reducing clicks by up to 62%.”
Shipley notes that security awareness and anti-phishing training, like all security controls, can’t reduce the risk from phishing to zero. But together, along with technologies such as email filters, modern authentication, and detection tools, they can help organizations be more resilient. When done well.
Speed and information overload
Two of the findings from this study speak to the need for different kinds of education, not just about how to spot a phish but how to work safely with electronic communications, from email to instant messaging and social media apps.
“Nearly 40% of all clicks are caused by people who are overwhelmed with emails and rushing or going into email autopilot and not reading the messages. Organizations could consider a cyber risk strategy that includes ensuring employees have enough time to carefully review emails and balancing internal communications to reduce cognitive overload,” says Shipley.
The danger of the dark side: the power of fear
The lowest selected self-reported answer to the question of why people clicked, “I thought I might get in trouble if I didn’t do it,” reveals a critical pattern of risky and undesirable behavior, with this group of respondents showing:
The highest overall Click Rate (12.1%) of all response groups;
The lowest Report Rate (19.5%) and;
The lowest Post-Click Report Rate (10.4%).
The fear-motivated group’s Click Rate was 26% higher, their Report Rate was 78% lower, and their Post-Click Report Rate was 58% lower than that of the best-performing groups.
“The low Post-Click Report Rate is particularly concerning and a possible measure of a lack of psychological safety. Organizations should watch that metric carefully, as people will still click on a well-crafted phishing email at vulnerable times. Making sure that their people feel comfortable admitting a mistake is critical for timely incident response,” says Shipley.
People who chose the option “I was expecting something similar” to the question on why they clicked had the lowest Click Rate of the response groups at 9.6%; people who chose the response “I was in a rush” had the highest Report Rate at 34.8% and the highest Post-Click Report Rate of 24.8%.
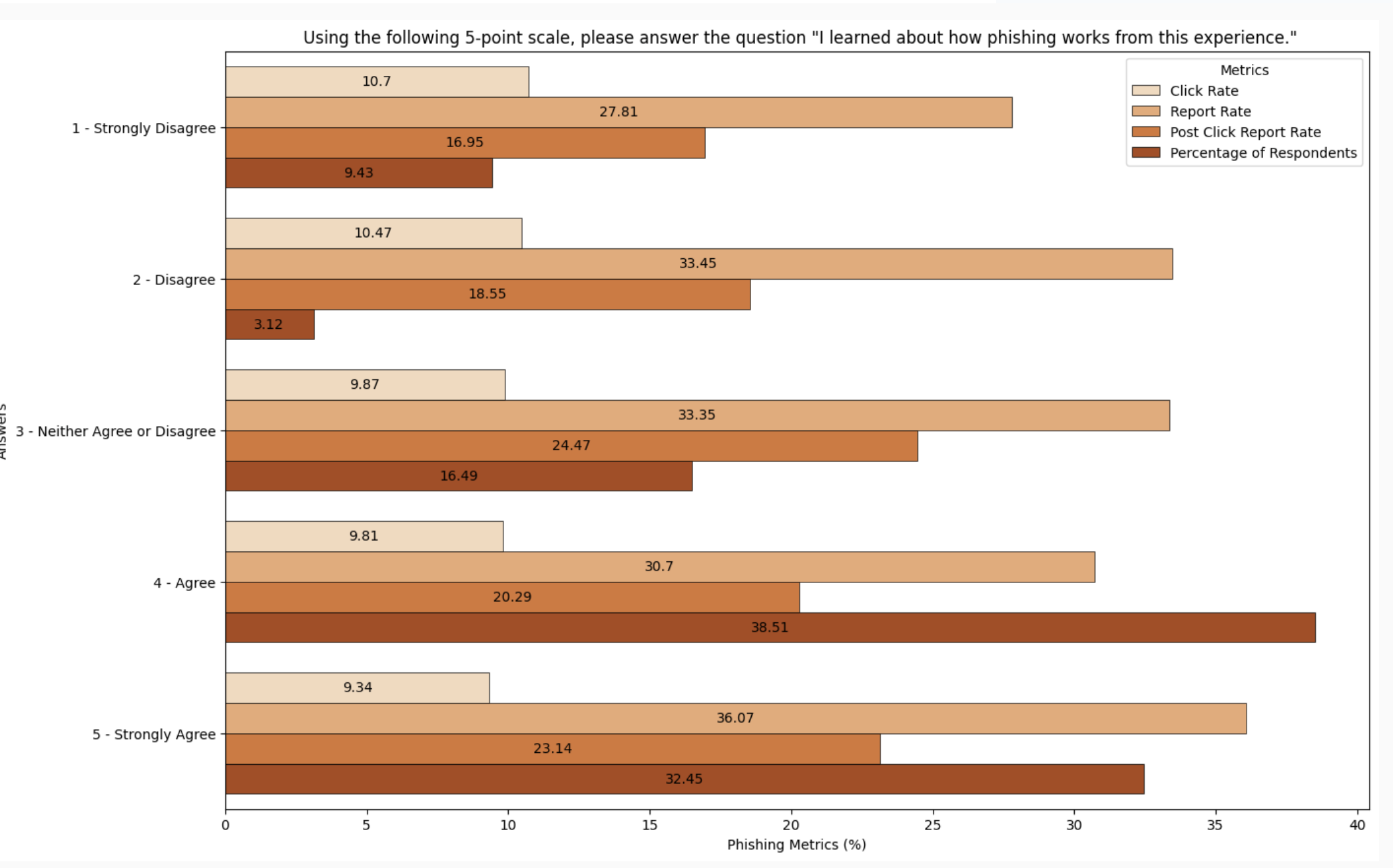
The majority of people report learning from phishing simulations
More than 70% of respondents agreed or strongly agreed with the statement “I learned how phishing works from this experience.”
Just under 13% of respondents disagreed or strongly disagreed with the statement, and they meant it; this group showed the highest Click Rates of any of the respondents to the statement.
“Phishing simulations work when done with modern remedial learning approaches, which include nudge-based messaging, assigned learning, and post-click questionnaires that encourage people to reflect on the experience,” said Shipley.
Shipley will share these insights and more in Toronto at Canada’s largest cybersecurity conference, SecTor, today, Wednesday, October 1st.
About Beauceron Security
Beauceron Security motivates people to make smarter technology choices so they can reduce cyber risk and thrive in a digital world.
Its technology helps organizations reduce human-centric cyber risk faster than traditional awareness programs and delivers the world’s leading security behavior and culture solution to organizations in every industry from 10 people to 100,000+.
Founded in 2016 by security professionals at the University of New Brunswick, Beauceron Security serves organizations of all sizes in every major industry. Its industry-leading Security Culture Score helps organizations understand not just what happened in awareness and anti-phishing programs, but also why people behave in risky ways — and how to improve risky behaviors and build positive security outcomes.